Top Data Security Threats Today
In today’s digital world, data security is essential because data is a company’s most valuable asset. Unless your company does not use any digital devices, the natural evolution of the workplace to a digitalized environment has enabled data is becoming the main source of competitive advantage for companies. Core data, in particular, is indispensable to every business as it may contain intellectual property rights, financial information, commercial secrets, or even operating data.
Core data is the heart of every business: it encapsulates a business’s operations, reputations, as well as income. Service shutdown caused by damaged core data will result in substantial business losses. Damaged data requires time and money to repair; studies point out that repair costs (including downtime, order loss, operating costs, etc.) have increased from an average of 1.16 million USD in 2020 to 2.34 million USD in 2021.
The Impact of Insider Attacks
With the advancement of computer and technological infrastructures, ransomware attacks have become increasingly widespread in this era of rapid growth. In particular, ransomware attacks have evolved into the most pressing issue in the year 2021. According to SonicWall’s cybersecurity reports, the volume of global ransomware attacks in the first half of 2021 alone has surpassed 304.7 million – a number that is more than double the total amount of attacks in 2020 (304.6 million), with about 151% percentage of year-to-date increase.
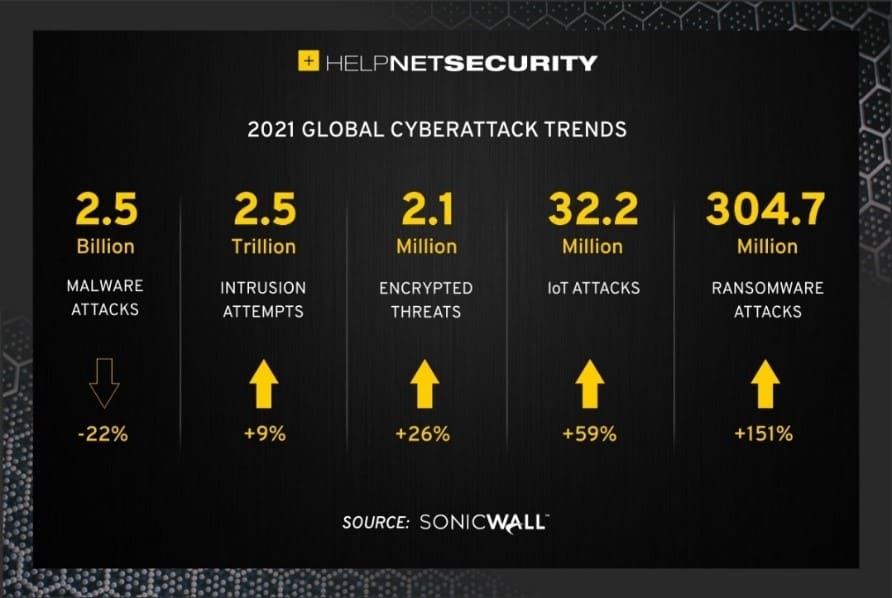
2021 Global Cyberattack trends
The Common data threats and the losses
As the saying goes, “know thy enemy”: to prevent data threats, we must first understand the source of these attacks. About 15% of data threats originate from distributed denial of service attacks (DDoS). DDoS employs a large amount of traffic to occupy a company’s network and resources in order to paralyze service, which in turn causes business shutdown and money losses. With each DDoS attack, losses can potentially surpass $40,000 each hour per breach, while total losses may surpass 500,000 US dollars.
The other 10% of data threat sources come from data breaches. Hackers use brute force attacks or spear-phishing attacks in order to gain unauthorized access to your data, threatening to disclose your core data, financial information, and intellectual property unless paid ransom. Every second around the world, at least 900 pieces of data are leaked, with an average loss estimated to be around $4M USD per large-scale data breach.
The most common data threat, comprising as high as 50% of all data threat sources, is ransomware, also known as denial-of-service attacks (DoS). The average total cost of recovery from ransomware attacks in 2021 is US$1.85 million. Only 8% of all US organizations managed to retrieve all compromised data after paying the ransom. Ransomware is spread through whale phishing techniques to fool employees into downloading malware. This malware encrypts core data thoroughly, essentially shutting down all company services whilst holding your data hostage.
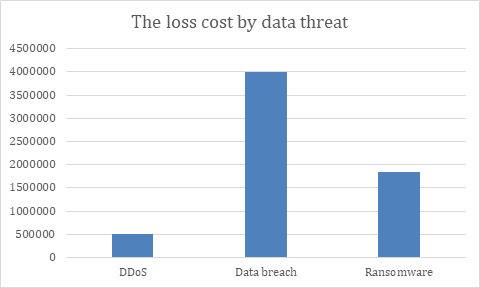
The table below displays the total amount of losses of the most common data threats. We can see that all sources of data threats target your core data and business services. By referencing this table to plan your complete security solution, you can reduce unnecessary expenses to zero.
| DDoS(15%) | Data breach(10%) | Ransomware(50%) | |
| Source | External net Botnet | Brute force Spear-phishing | Brute force Whale-phishing |
| Method | Occupy system resources | Steal core data | Lock/delete core data |
| Losses | Business shutdown | Core data loss Business shutdown | Core data loss Business shutdown |
The sources, methods, and losses of the most common data threats.
The solution: Enterprise Level of Data Security
The best way to prevent the complete destruction of your data brought by these threats is to prepare in advance. If you are well prepared, you can avoid major losses and damages. QSAN combines years of storage equipment and data security experience to compile for you our Security Trilogy in order to assist you in better protecting your business core data.
The first part: Core Data Protection
The biggest hidden cost of recovering from data threats is downtime. Therefore, the best protection is prevention. Through access control and data encryption, this initial defense can keep any malware away from business services and fully protect core data safe.
The second part: Local Fast Recovery
If a data threat really happened, using a local backup to recover or replace your service can greatly reduce RTO to almost 0. By doing local synchronization or snapshot, you can backup core data without affecting system performance. Also, set the backup to real-time to make sure the recovery reaches 100% and reach almost 0 RPO.
The third part: Offsite backup protection
When the local system falls, the fastest way to recover is through Remote backup. A good remote backup can help you restore data and maintain service to avoid downtime. Through high-level remote backup protection, we can reduce RTO in hours and RPO to 24 hours.
We will introduce in further blog posts how to prevent data threats and quickly restore services through our Security Trilogy, as well as how to reduce the biggest cost of data threats: downtime.
Proactive Data Security Best Practices
The blog post is the first in our QSAN Security Trilogy that discusses the importance of core data and the prevention of data threats. To maintain business continuity and trust, organizations must prioritize data security as a long-term investment, not just a compliance checkbox. By following the QSAN Security Trilogy, you can recover quickly from an attack and avoid business downtime.
It is best to read and follow along with the Trilogy in its sequential order:
- Core Data Protection that you can use for preventing any data threats.
- Smart Quick Recovery helps you shrink RTO to a minimum.
- Offsite Recovery protects your service even when your local system is attacked.
To learn more about the QSAN Security Trilogy for ransomware, check out these additional resources:



